
In July 2025, Vladimir Putin proudly oversaw the commissioning of the Knyaz Pozharsky at a Northern Fleet base in the Arctic, presenting it as a symbol of Russia’s modern military power. This Borei-A class submarine, worth an estimated 1–2 billion dollars, was designed to patrol silently under the polar ice, carrying missiles capable of striking targets thousands of kilometers away.
Russian state media framed the event as proof that Western sanctions could not halt Moscow’s rearmament, calling the submarine one of the pillars of our strategic stability” Yet, within days of the ceremony, Ukrainian cyber operators quietly broke into Russian systems linked to the vessel, setting the stage for a leak that would spill some of the most sensitive undersea secrets Russia possesses.
Why These Submarines Matter Most

Russia’s nuclear strategy depends heavily on submarines that can disappear under Arctic waters and stay hidden for months. The Borei-A class sits at the heart of that plan: each submarine can carry up to 16 Bulava submarine-launched ballistic missiles, each missile able to deliver multiple nuclear warheads over intercontinental distances.
Experts estimate that the five improved Borei-A boats together account for roughly a third of Russia’s deployed sea-based nuclear firepower, making them central to Moscow’s ability to threaten the United States and Europe even if land bases are hit.
Life Inside a Nuclear Submarine
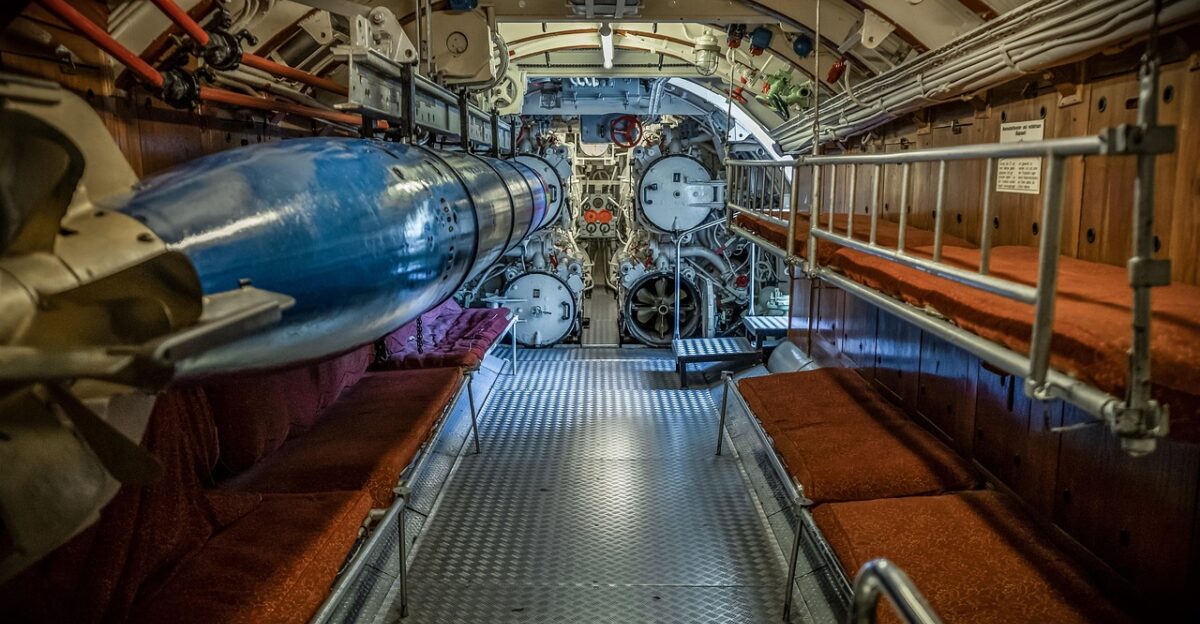
Ballistic missile submarines like the Borei-A are built around one core idea: stay hidden, stay alive, and stay ready. Their hulls are divided into watertight compartments, lined with sensors, fire-suppression systems, and backup controls so that the boat can survive damage that would sink a normal vessel. Every hatch, pipe, and cable route is drawn in classified diagrams that adversaries desperately want to see, because those blueprints reveal where emergency systems might fail or where a single hit could cripple the ship.
The Knyaz Pozharsky, with a crew of just over 100 sailors, was meant to be one of the quietest and most automated submarines Russia has ever built. A European naval analyst quoted in National Security News said the submarine was “intended to disappear into the noise of the Arctic seas, practically invisible to NATO sonar when operating as planned.”
A Dangerous Early Weak Spot
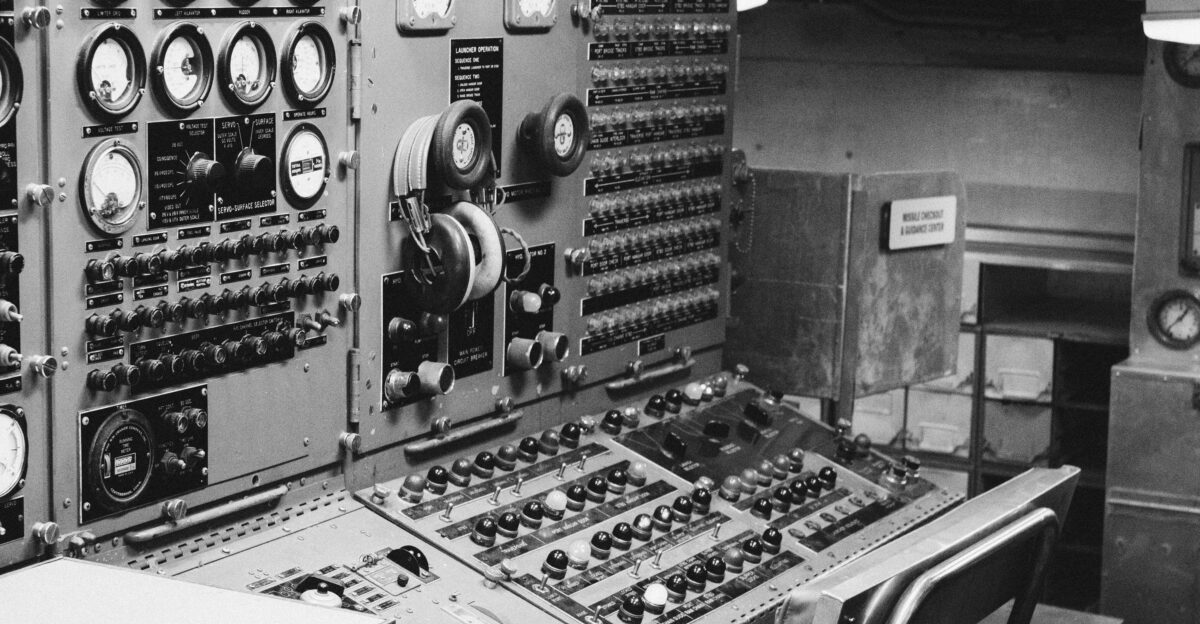
New warships are most vulnerable in the months just after they enter service, when crews are still training and systems are being tested. During this phase, engineers, officers, and contractors constantly exchange documents, test reports, and manuals across military networks, often under time pressure and sometimes with weaker cyber safeguards.
The Knyaz Pozharsky was in exactly this “shakedown” period in late July 2025, still cycling through trials when Ukrainian and allied cyber specialists began probing connected Russian systems. Security researchers later noted that Russia appeared to rely heavily on centralized digital document repositories for the Northern Fleet, creating a tempting single point of failure.
The Hack Goes Public

On August 3, 2025, Ukraine’s military intelligence service, known as HUR, went public with a stunning claim: it had hacked Russia’s newest nuclear missile submarine and stolen its secrets. The agency posted scans and excerpts of what it said were Russian Navy documents, including technical descriptions, command procedures, and crew information tied to the Knyaz Pozharsky.
In a statement, HUR said the operation had allowed it to obtain data “that reveal the features and technical limitations” of Russia’s latest strategic submarine. National Security News reported that the leak dropped just 10 days after the submarine’s commissioning, catching Russian officials off guard and forcing an emergency damage assessment inside the Ministry of Defense.
A Blueprint of Weaknesses

The leaked files did not just offer a few isolated details, they painted an almost complete picture of how the Knyaz Pozharsky is built and operated. Documents included crew rosters listing sailors by name, rank, and physical fitness assessments, giving insight into the human side of the submarine’s readiness.
Technical diagrams showed where critical systems sit: ballast tanks, watertight doors, firefighting lines, wiring trunks, and communications nodes that connect the boat to Russian command. Operational schedules outlined planned patrols, training cycles, and likely deployment patterns.
An Intelligence Gift to NATO

Because HUR chose to publish much of the stolen material openly, NATO and partner navies did not need to run their own risky operations to access it. Intelligence analysts in the United States, Britain, and across northern Europe quickly began comparing the leaked diagrams with existing acoustic data and satellite imagery, refining their models of how Borei-A submarines move, sound, and respond under stress.
A cyber brief by Europe’s cybersecurity response team noted that the “public exposure of sensitive design information significantly lowers the cost and time needed for adversaries to develop targeted countermeasures.” Put simply, NATO can now tweak sonar algorithms, adjust patrol routes, and refine anti-submarine tactics with real data instead of assumptions.
When Nuclear Threats Lose Their Mystery

Nuclear deterrence depends on both capability and uncertainty: rivals must be sure you can hit back, but unsure how and from where. Sea-based nuclear forces are designed to provide that uncertainty, hiding in the world’s oceans to guarantee a survivable second strike if war ever breaks out. By exposing detailed information on the Borei-A design and operations, Ukraine has chipped away at that uncertainty for a key part of Russia’s arsenal.
Analysts quoted by National Security News argue that Moscow now has to assume NATO understands critical weaknesses and may be able to track or target these submarines more effectively than before.
The Ten-Billion-Dollar Problem

Ballistic missile submarines are among the most expensive weapons any state can build, and the Borei-A class is no exception. Estimates from defense industry sources suggest each improved Borei-A boat costs between one and two billion dollars to construct and equip, even before counting the missiles they carry. With five of these submarines in service or nearing completion, Russia has likely invested around 10 billion dollars into this single slice of its nuclear triad.
The cyberattack did not sink those vessels, but it damaged their strategic value by forcing Moscow to consider costly fixes: redesigning systems, altering procedures, retraining crews, and in some cases possibly limiting missions.
A Whole Class Put at Risk

Perhaps the most alarming detail from HUR’s statement was its claim that the stolen information does not apply only to the Knyaz Pozharsky. The agency said the documents shed light on “features and technical limitations” of other submarines in the same Project 955A series, meaning the leak may expose shared design choices across the entire improved Borei-A class.
Because these submarines are built to a common blueprint, vulnerabilities in one often exist in all. National Security News reported that Western officials now treat the whole Borei-A fleet as “potentially compromised” from a security standpoint, even if Russia makes adjustments.
Kremlin Scramble Behind Closed Doors

Inside Russia’s defense establishment, the leak triggered a frantic effort to understand the damage. Investigators must determine which networks were breached, how long intruders were inside, and whether the hack extended beyond submarine files into other strategic programs. Cyber forensics teams are reportedly combing through server logs and communications to trace the path of the intrusion, while naval officers review operating procedures to find gaps in security discipline.
CERT-EU’s August 2025 brief noted that Russian authorities appeared to react by tightening access controls and shifting some sensitive systems offline, a sign of serious concern about further exposure.
Ukraine’s Message to Moscow and the West

By choosing to announce the hack instead of keeping it secret, Ukraine turned a quiet cyber operation into a global information strike. HUR’s public statement framed the breach as a blow against “the imperial myth of the aggressor state Russia,” casting the operation as proof that Moscow’s most prized weapons are not untouchable.
Ukrainian officials emphasized that the hack showcased their ability to hit strategic targets far beyond the front lines, reinforcing Kyiv’s argument that it is not just defending itself but actively degrading Russia’s war machine. Commentators in Kyiv also noted the domestic impact: stories of a successful strike on a nuclear submarine boosted morale after months of grinding warfare.
A Quiet Edge for Western Navies

While Ukrainian officials spoke publicly, NATO governments largely stayed silent about how they would use the leaked data. Behind the scenes, however, Western navies are believed to be feeding the information into simulations, acoustic libraries, and war game scenarios focused on the Arctic and North Atlantic.
The CSIS think tank has described such episodes as part of a broader “shadow war” in which cyber operations, intelligence leaks, and infrastructure mapping steadily reshape the military balance without open clashes. In this case, NATO’s “quiet advantage” lies in knowing more about how Russian strategic submarines are likely to behave and fail in real-world conditions.
Costly Fixes, Hard Choices

The Kremlin now faces a dilemma with no easy answer. To fully address the exposed weaknesses, Russia would have to pull Borei-A submarines into shipyards for significant upgrades, redesign some systems, and retrain entire crews, a process that would cost billions and reduce the number of available boats for years. Alternatively, Moscow could rely on partial fixes while keeping the submarines on patrol, hoping that changes in tactics and communications are enough to offset NATO’s new insights.
Arms-control experts say either choice weakens Russia’s near-term deterrent, because every day spent in dock or under suspicion reduces confidence in those submarines’ survivability. “Modernization was supposed to strengthen Russia’s nuclear shield,” one SIPRI analyst observed. “Instead, this episode shows how digital vulnerabilities can hollow it out from the inside.”
A New Era for Submarine Secrecy

The Knyaz Pozharsky hack has become a warning sign for navies far beyond Russia and Ukraine. For decades, submarine security relied on physical isolation, classified blueprints, and the difficulty of tracking vessels in deep water. The 2025 breach shows that digital weaknesses in shore-based networks, document systems, and training pipelines can pierce that shield without ever touching the submarine itself.
Military planners now must assume that any major platform, no matter how secret, can be compromised if its data is exposed through cyber operations. As one Western cybersecurity official told a researcher, “If Russia’s newest nuclear submarine can be laid bare less than two weeks after it sails, no one can pretend their systems are truly safe anymore.”
Sources:
National Security News, “Ukrainian intelligence agency steals Russian nuclear sub secrets in a cyber attack,” 5 August 2025
CERT-EU, “Cyber Brief 25-09,” 1 August 2025
United24 Media, “Ukraine Gains Secrets of Russia’s Newest Nuclear Sub ‘Knyaz Pozharsky’,” 2 August 2025
Business Insider, “Ukraine Stole Intel, Found Russian Submarine Weak Points,” 4 August 2025
CSIS, “Russia’s Shadow War Against the West,” 17 March 2025
Army Recognition, “New Nuclear Submarine Knyaz Pozharsky Projects Russian Nuclear Power into Arctic,” 4 November 2025